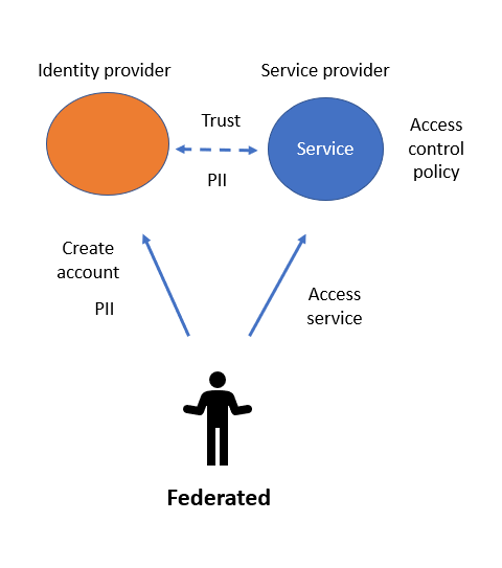
Why Should You Tokenize Sensitive Data Like PII, Credit Card? - Strac - Detect & Mask Sensitive Personal Data
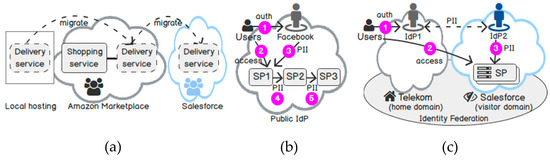
Future Internet | Free Full-Text | Identity-as-a-Service: An Adaptive Security Infrastructure and Privacy-Preserving User Identity for the Cloud Environment
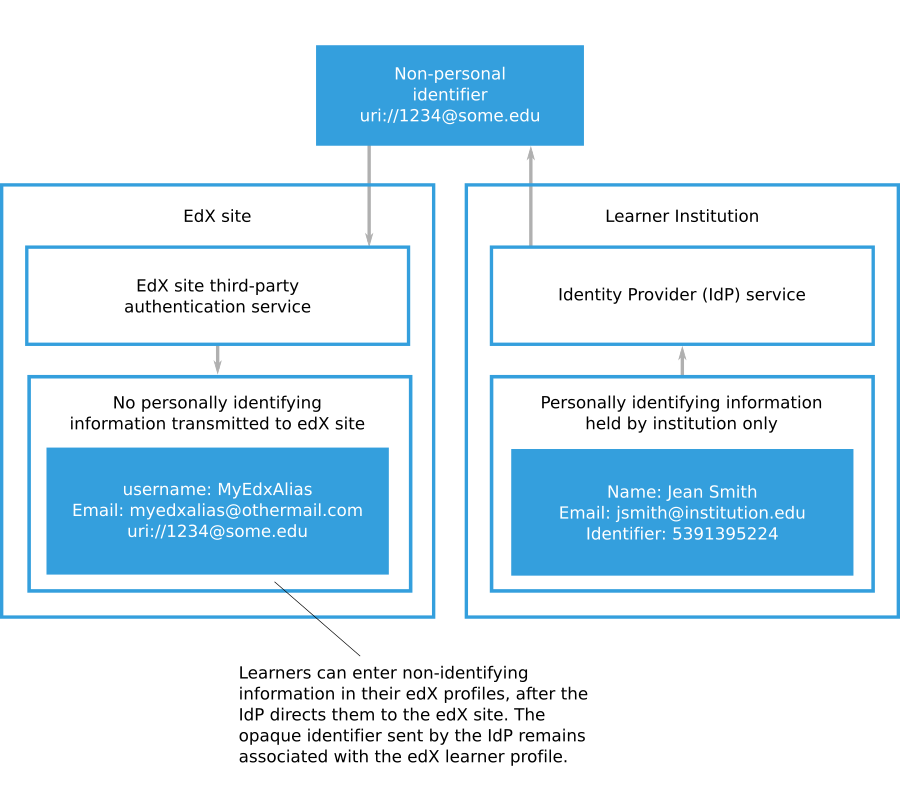
4.23.6. Eliminating PII From Third-Party Authentication — Installing, Configuring, and Running the Open edX Platform documentation

Implement the On Behalf Of flow between an Azure AD protected API and an API protected using OpenIddict | Software Engineering


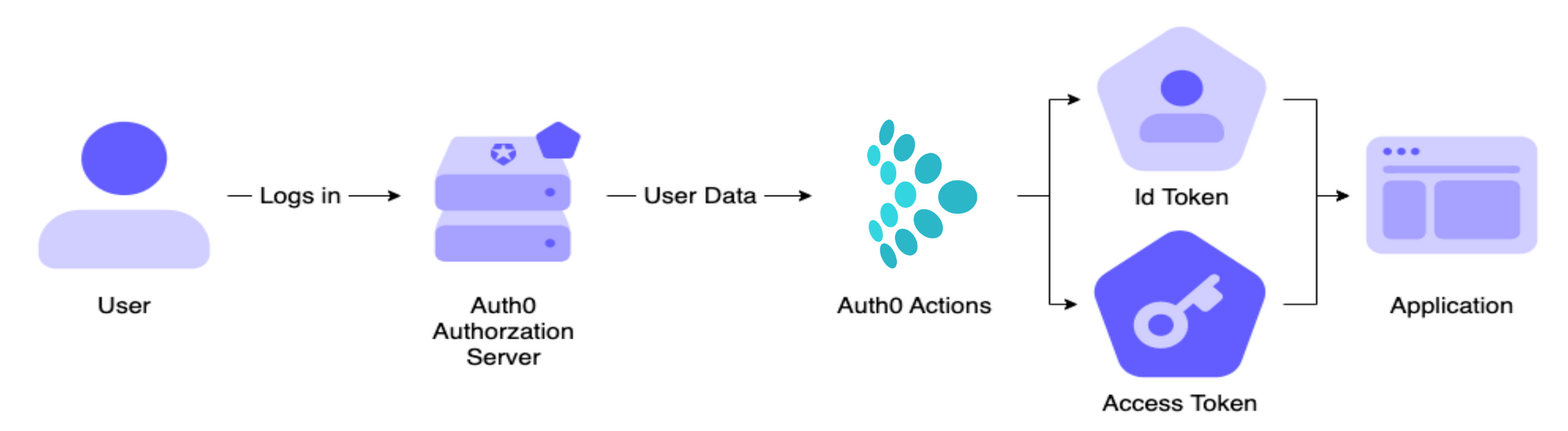
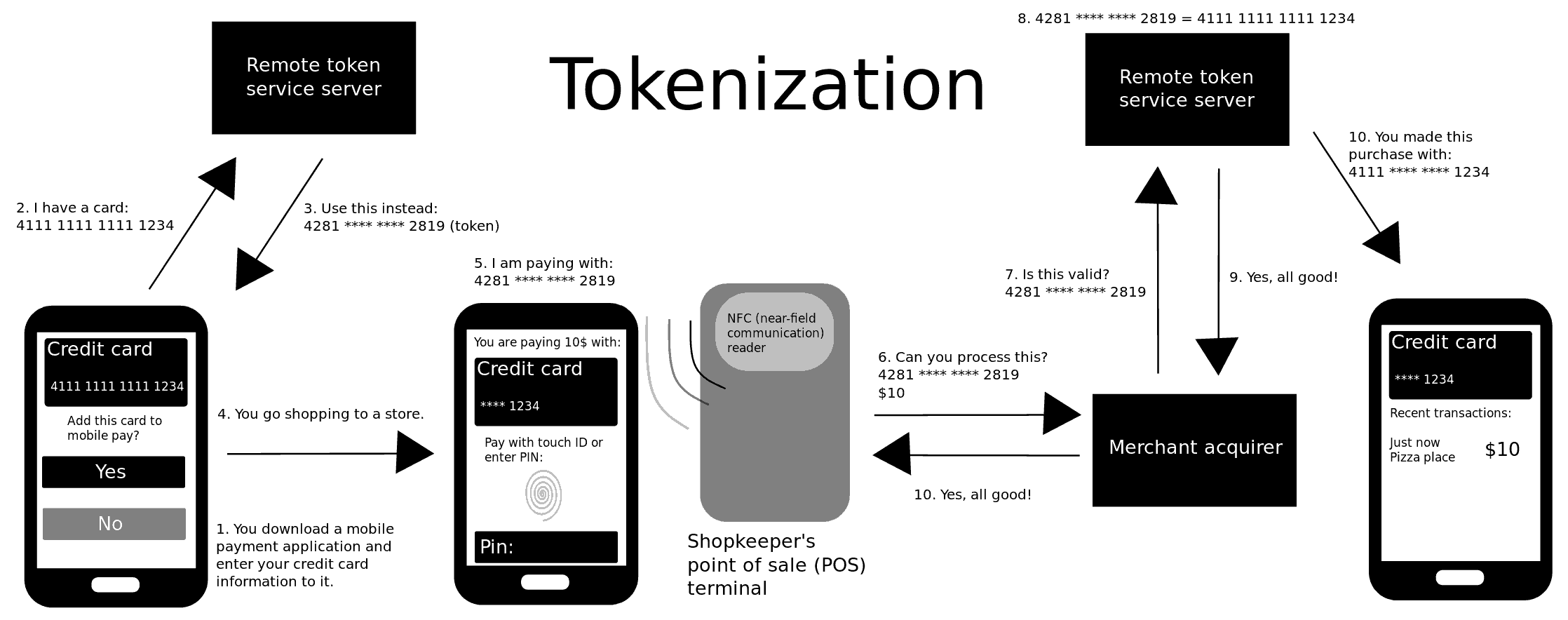
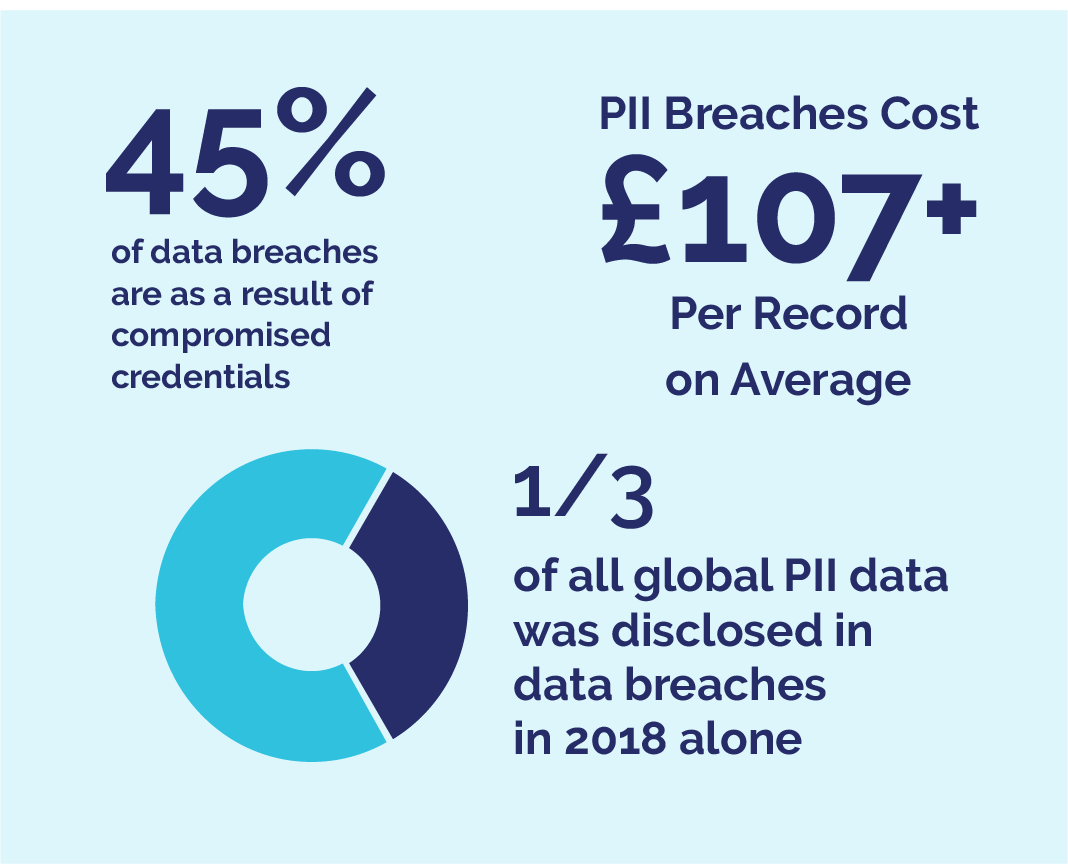



.jpeg)